One mistake that should never be made is to assume permissions and identity access are easy. If you plan on just throwing some rows in the database and then making an authorization decision based on the existence (or nonexistence) of a row… then you might not be “secure”. And further, once you are successful, you should also start to consider a scalable and more accurate approach.
Identity and access management (IAM) is a critical part of an application (Security! Compliance!). When done correctly IAM can reduce operational spend and allow your business to tackle new initiatives with a more agile approach. Unfortunately, building permission systems — even basic ones — can be an overwhelming task and probably something that should be outsourced to the “right” platform.
The founders of Authzed (Jake Moshenko, Joey Schorr and Jimmy Zelinskie) saw many developers struggling to build permissions into their applications and they knew there had to be a better way. In this short interview, Jake explains a bit about how they have made some crucial decisions in their tech stack:
The inception of a Zanzibar-inspired database
In 2019, Google released the Zanzibar paper. The research described how to take the best concepts from distributed systems and combine them with a reliable, performant system with no single points of failure — that also happens to be infinitely horizontally scalable.
Following the release of the paper, Jake, Joey, and Jimmy sought to see how this approach could help build a more effective IAM function in their open-source project, Quay (the first private Docker registry). They had already integrated basic permission controls into Quay, but they were nowhere near the level of Zanzibar.
They realized the value in the Zanzibar approach and started to consider how distributed permissions could help them. They came up with the following value system for this approach:
- Always correct decisions
- Uniform security model across their polyglot services and applications
- Reliable and always-on access to the platform
- Scale permissions and controls as they grow and as far as they grow
- Highly performant, low latency permission checks
One other final requirement: they wanted to create a platform that was significantly more approachable and less daunting than Zanzibar.
In 2021, they launched Authzed with the intent to build out a Zanzibar inspired IAM platform and help further the concept of GIFEE (Google Infrastructure For Everyone Else). They built an open source implementation of Zanzibar called SpiceDB, an open-source database system for managing security-critical application permissions. And recently, they launched their Authzed managed service, which delivers a fully managed platform to validate application permissions.
How can Authzed and SpiceDB help me with permissions?
Modern IAM solutions all have a similar goal: to decouple policy from the application. SpiceDB takes this one step further by also decoupling the data that policies operate on. This means that SpiceDB creates a single unified view of permissions across all of your organization’s applications.
This strategy has become an industry best-practice and is being used at companies large (like Airbnb) and small (like Carta). However, there are a few aspects of SpiceDB that make it unique from other solutions:
Build with optimal flexibility.
The SpiceDB schema language is built on top of the concept of a graph of relationships between objects. This ReBAC design is capable of efficiently supporting all popular access control models (such as RBAC and ABAC) and custom models that contain hybrid behavior. By developing a SpiceDB schema, you can iterate far more quickly and test designs before altering the application code.
Model the user yourself, and bring in different users from different sources.
SpiceDB is “identity vendor-neutral” meaning you can use multiple identity providers (like Auth0 and Okta) together and ask questions of different heterogeneous user sets. This capability is not possible today in Zanzibar.
Run global deployments without having to pay the costs.
SpiceDB has support for globally replicated backends, meaning that you can run this service all over the globe as a single, globally-deployed permissions database. It’s cost-effective because they share that single cluster with multiple users and federated out into smaller chunks. So you get the benefit of being globally deployed without the costs.
[Watch the team demo Authzed here: https://authzed.com/demo ]
What does SpiceDB look like under the hood?
SpiceDB acts as a centralized service that stores authorization data. Developers create a schema that models their permissions requirements, use a client library to apply the schema to the database, and insert data into the database.
Once stored, data can be performantly queried to check permissions in your applications. You can answer questions such as “Does this user have access to this resource?” and “What are all the resources this user has access to?”
Since SpiceDB is an open-source version of Google’s Zanzibar model, many of Zanzibar’s major design concepts exist in SpiceDB. It starts with the life of a request which is handled by the dispatch interface and then persisted into a datastore. Here’s a high-level architecture overview of a SpiceDB deployment:
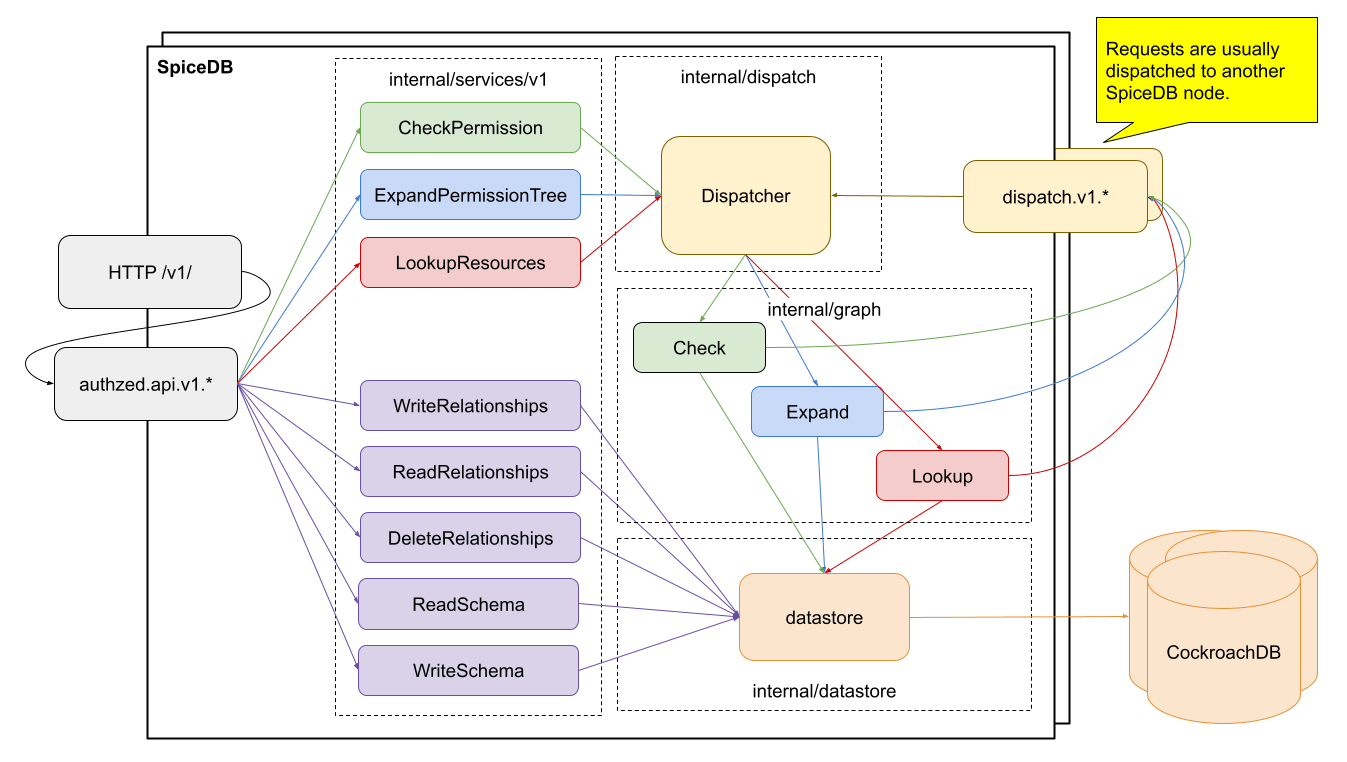
(Credit: Authzed blog post The Architecture of SpiceDB)
And, yes, SpiceDB is a database — but it’s a purpose-built graph database for computing and commissions. This means there is still a need for a distributed backend store for the relational data to allow performing generalized queries.
Zanzibar uses Spanner as its backend distributed datastore. Spanner delivers low latency, high availability, immediate consistency, and ACID transactions. The team at Authzed wanted a Spanner replacement that would provide the same capabilities, and their search ultimately led them to CockroachDB. Similar to Authzed, CockroachDB is another GIFEE company (with some differences of course) that gives developers the freedom to deploy anywhere across any cloud – no vendor lock-in.
With support from CockroachDB, SpiceDB’s storage backends have a Spanner equivalent which gives users globally distributed data with ACID semantics. (If you would like to hear more about why Authzed chose to build on CockroachDB, check out this video: How Authzed Built an OSS, Zanzibar-Inspired Permissions Database).
Get started with Authzed and SpiceDB today!
SpiceDB is open-source and free to use: click here. If you are interested in having Authzed set up and manage SpiceDB for you, get in touch with their team. You can also check out this demo.
Have questions for the community? Authzed has a Discord where you can join the discussion. They also have a playground available for modeling and testing permissions. Try it out for yourself!
Thank you to Authzed’s Jake Moshenko (co-founder) and Even Cordell (software engineer) for providing the information for this post. Check out this video from RoachFest ‘22 to watch Jake explain how to build fine-grained application permissions with CockroachDB: